Users
Tier 1, Tier 2 and Tier 3 threat analysts.
Objective
As the lead designer for Endpoint, my focus was on creating a cohesive vision aligned with overall NetWitness, simplify ECAT's complex workflows and plan the design deliverables across multiple sprints for its integration into NetWitness.
I took on the role for integrating 10+ Ecat's complex features like File status and Blocking, File Download and Analyse, Anomaly Detection, MFT (Master File Table) and Memory Dump, Certificates View and Blocking, Hosts and Files Dashboard while also designing scalable and re-usable interaction and visual design patterns. This meant continuous conversations with Product manager and champions (including threat hunters) to understand the domain and the current tools capabilities and features.
My Role
Design Lead along with a junior designer. Responsible for guidance, setting up vision, refine features and build patterns and standards for Endpoint features that can scale and be re-used by other designers and scrum teams. Designed for over 5 major successful releases.
Act as UX champion by leading the conversations from "is it technically feasible" / "how long will it take to build" to "how does the user use this feature and what do they feel about it" at a leadership and scrum team level
Conduct (both remote and onsite) contextual inquiry sessions to learn and understand threat hunter workflows, requirements and partner with PMs on funneling their feedback into deliverables
Collaborate with product management, SMEs (threat hunters) and engineering architects on defining and refining features and functionalities
Co-ordinate with scrum teams to prioritise UI backlogs and groom stories for next releases. Also worked extensively with QE to test built features
Co-ordinate with content developers to standardise and unify the interface messaging
Product Information
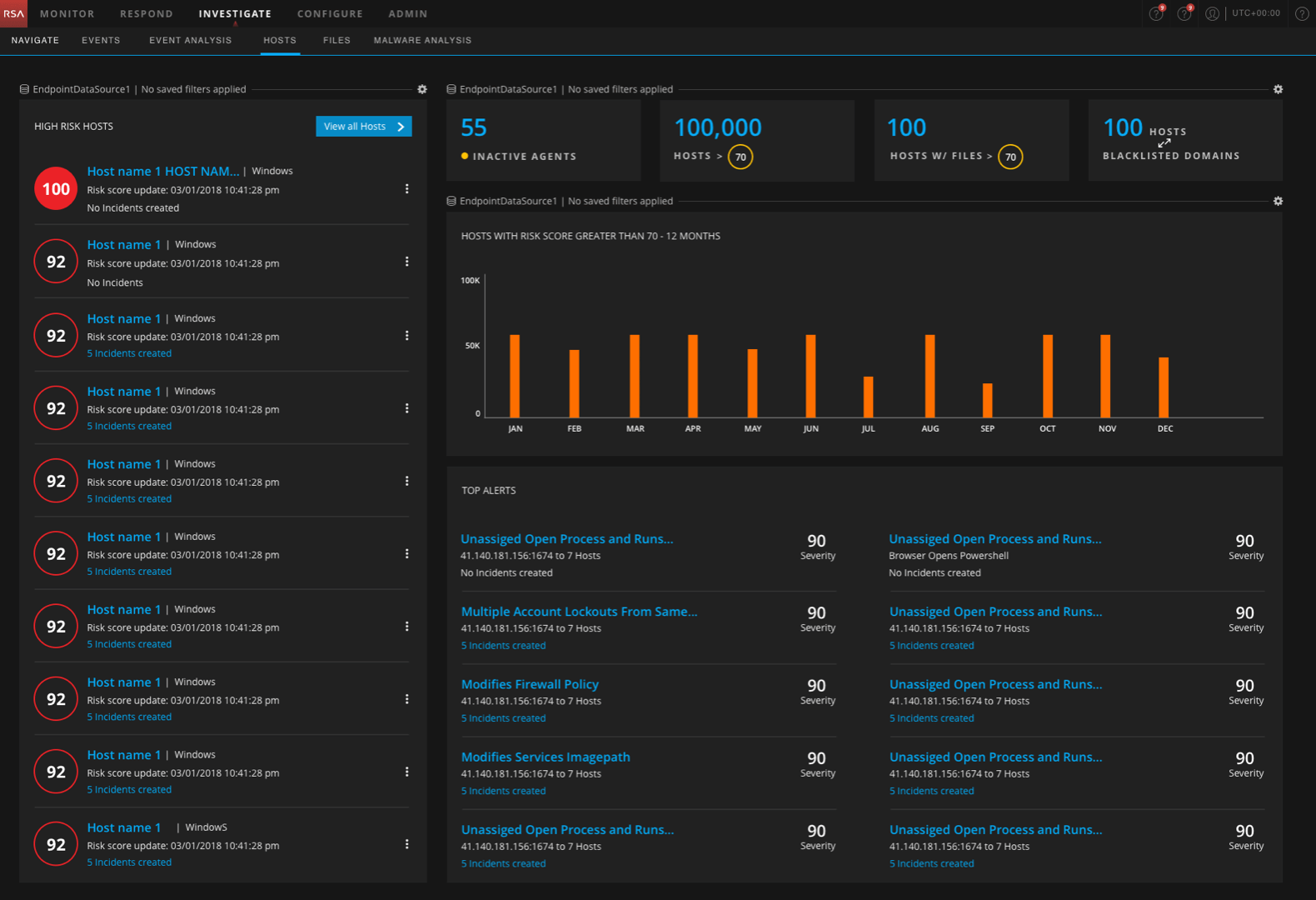
Netwitness has Logs and Packets as a browser based tool which collects and analyzes logs, network packets, NetFlow, and endpoint data. ECAT, a desktop application and separate product, is an endpoint threat detection and response solution that exposes targeted, advanced malware, highlights suspicious activity for investigation, and instantly determines the scope of a compromise to help security teams stop advanced threats faster. Users of ECAT, while they appreciated the tool’s capabilities, found the tool to be extremely complicated and mostly never knew of its powerful functionalities. In the previous release, a basic view of Files, Hosts and its details (Modules and Machines in ECAT) was built into Netwitness.
Challenges
Domain complexity was a huge challenge. While my previous stint was also with a security company (Symantec) the domain there was Website security while at RSA it was Endpoint and network related. Netwitness’ next big release was planned for March ’19 and one of the primary focusses was its Endpoint features. Thus, I faced an uphill task of understanding the domain, simplifying the workflows and delivering the design solutions while still validating them, all within a crunched timeline.
Engineering complexity also meant that I had to be careful with my design decisions to ensure solutions didn’t complicate the experience. Part of my responsibility was also to build a good rapport with the scrums team as local presence was limited and the expectations from the release was high. Multiple meetings with PM/engineering leads were required for me to understand product nuances (and its limitations).
While we had design patterns and standards, they were at a basic level and there was a lot of inconsistencies in the way they were implemented. Also the current implementation in Respond and the existing Hosts and Files pages didn’t cover a lot of use cases that were essential for the new set of features. Thus, I had to design new interactions and patterns which then became standard across other Endpoint and UEBA screens.
Contextual Inquiry
A security operations center (SOC) is a facility that houses an information security team responsible for monitoring and analyzing an organization’s security posture on an ongoing basis. The SOC team’s goal is to detect, analyze, and respond to cybersecurity incidents using a combination of technology solutions and a strong set of processes.
from digitalguardian.com

I had the opportunity to visit and interact with the Dell’s SOC team situated within the same building as ours, where I was greeted by a similar sight to the image above. Some interesting insights I gathered :
Performance was one of the key areas that an analyst / admin measured the experience of our product. For a data and resource heavy solution like NetWitness that runs on the browser, being able to query & sift through large amounts of meta data and take mitigation actions in bulk meant that analysts could simplify their workflows and take corrective actions much faster than depending on Command Line interfaces.
Often NetWitness (and other security products) are used in conjunction with other popular security products to form a chain of workflows with handoffs through integrations depending on the contractual agreements of the customer. As designers, apart from end to end experience of a feature we also have to factor in scenarios where our product / feature could be part of bigger workflows.
I also realised why providing dark & light themes for our interface was important to their experience because often analysts / admins sit in low light conditions with 3 – 6 monitors and providing dark theme greatly reduced the glare and made it easy on their eyes. At the same time, they would also project their screens on to a large monitor or wall for collaboration, and here the light theme did a great job of highlighting the details that usually a dark theme screen would lose out on. Providing both gave them best of both worlds.
While reviewing features with them, I realised NetWitness product was geared to the more experienced Analysts / Admins even though in reality there are fewer of them and the industry itself was moving towards a more generalised role, especially in the small / medium companies. This meant reviewing these features with L1 & L2 analysts would often lead to confusing feedback where they weren’t able to understand the importance of the features or perceived the overall interface to be complex.
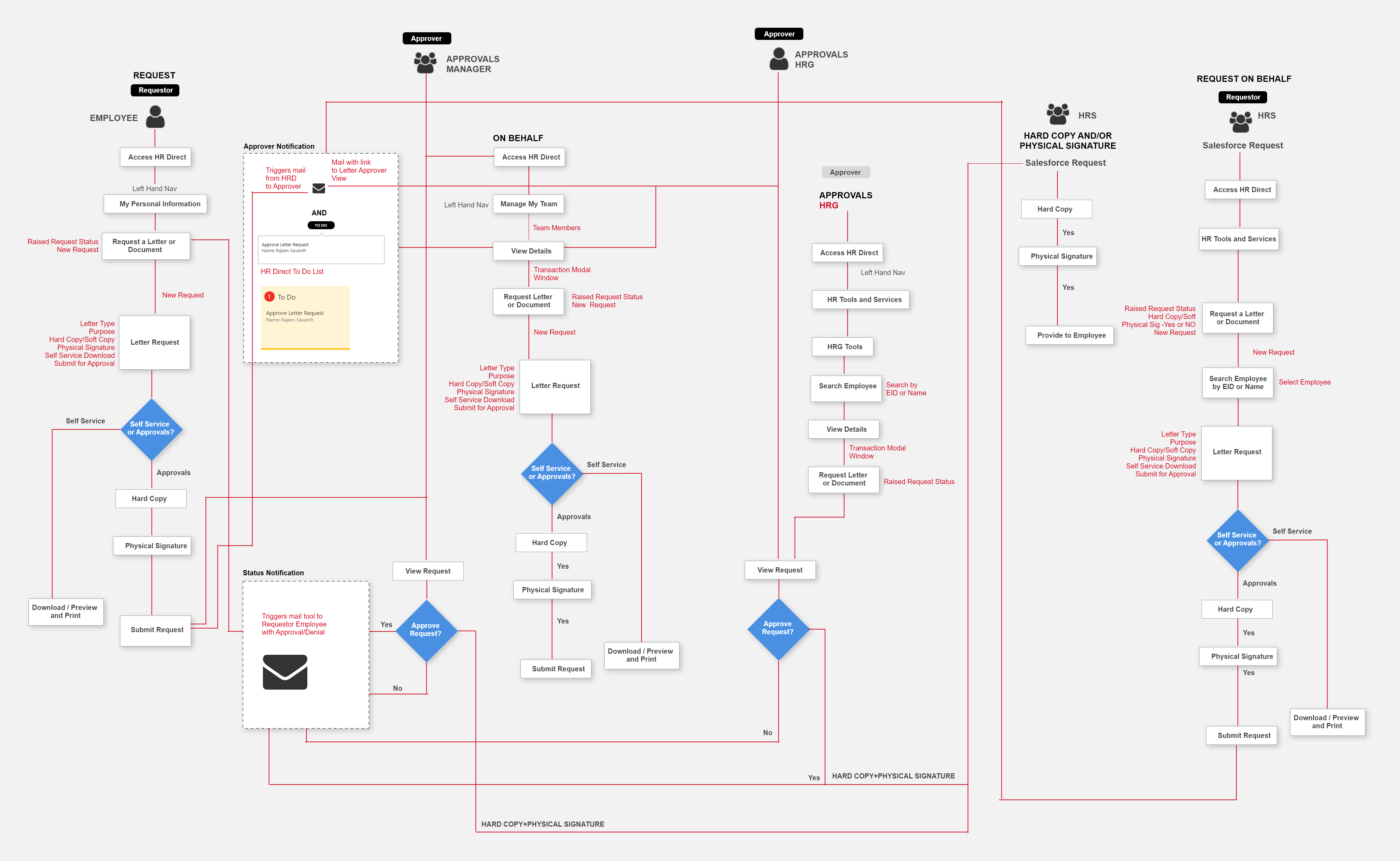
ECAT
Information Architecture
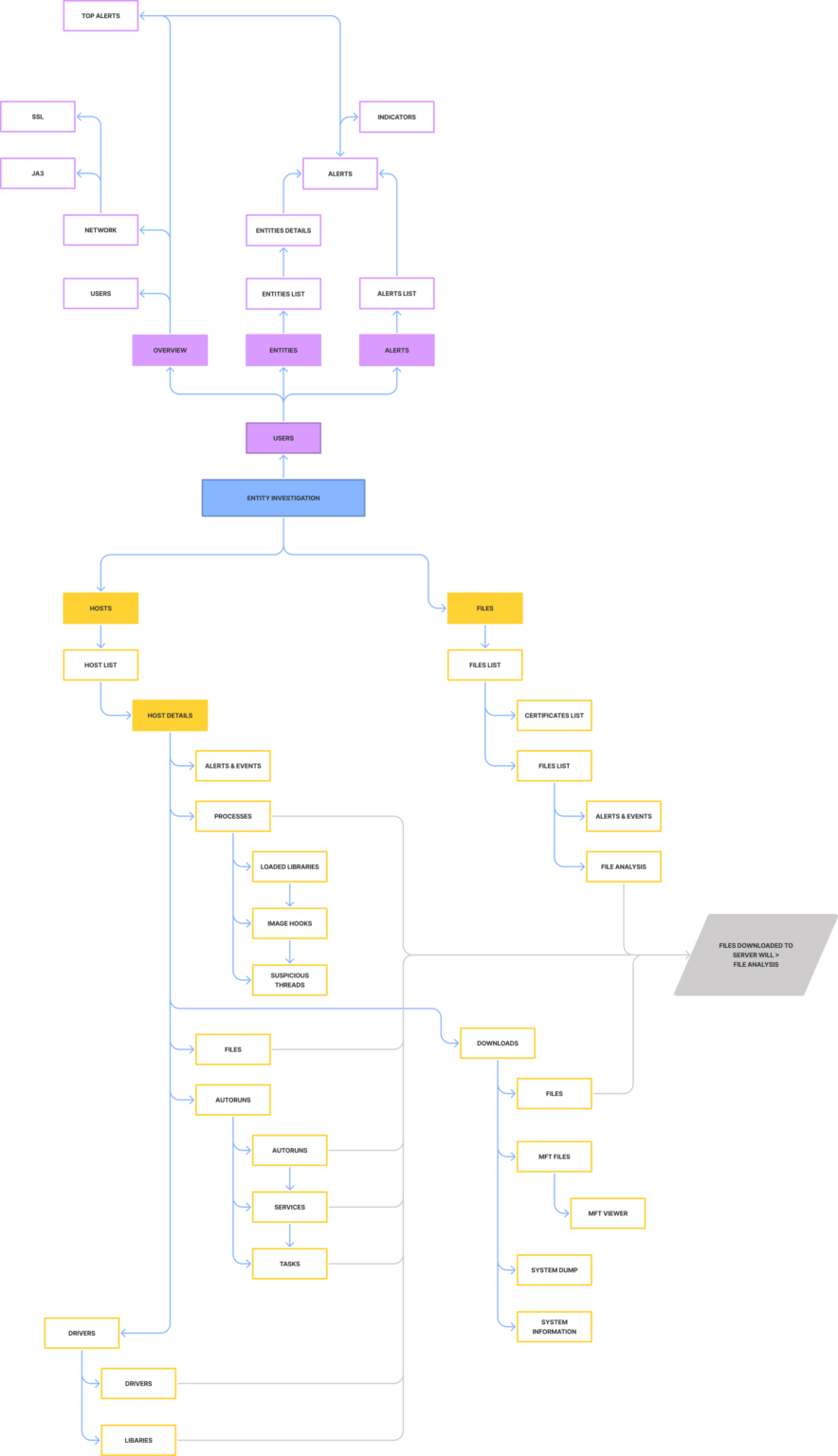
I laid out all the pieces related to the main entities (hosts, files and users) in a threat investigation and created a structure and hierarchy between them. This helped me in understanding and building new workflows for the analyst and define the user interface that helped the user complete their task and achieve their goal.
It also integrated two totally separate and acquired solutions (Endpoint and UEBA) together and inline with the overall Netwitness product even though I worked with two sets of engineering, PMs and architecture teams situated in Bangalore and Israel.
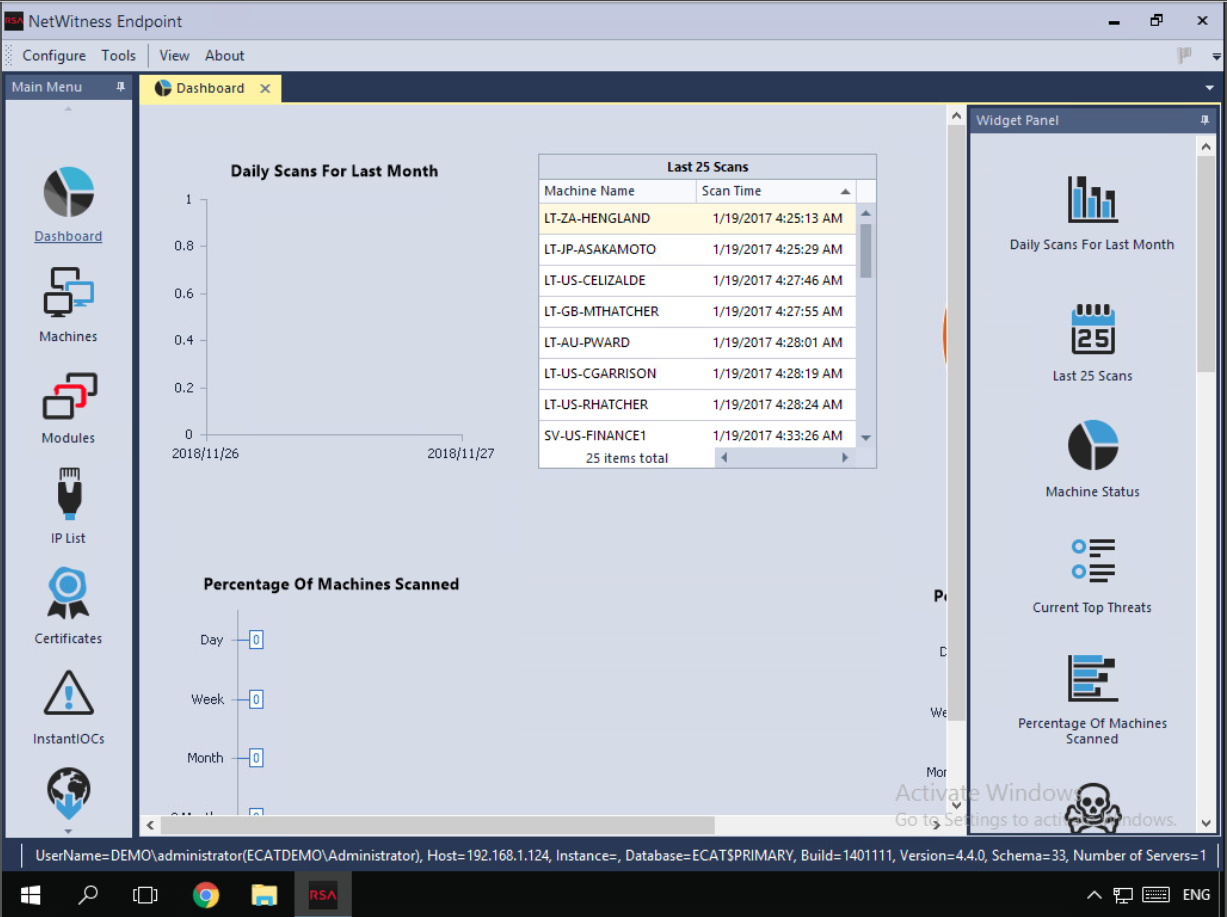
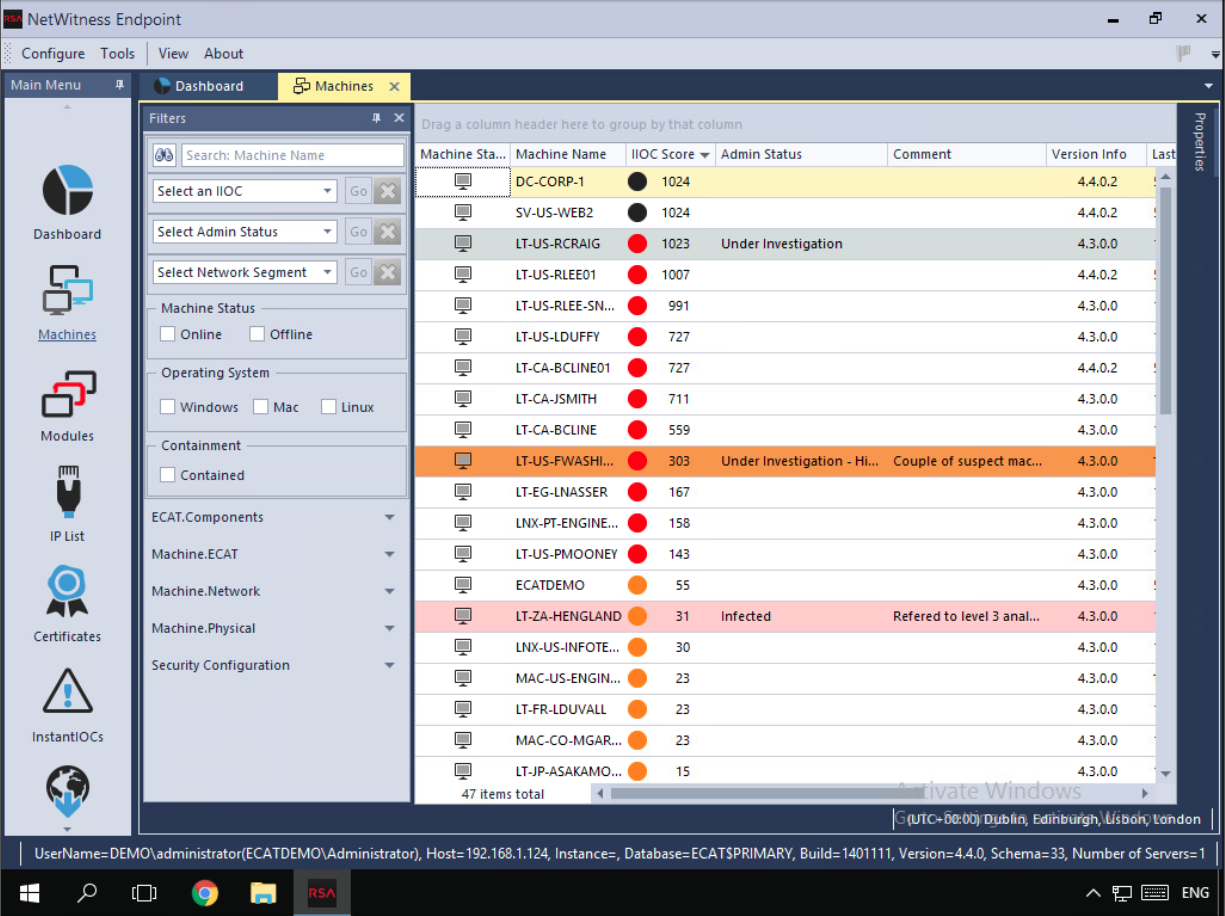
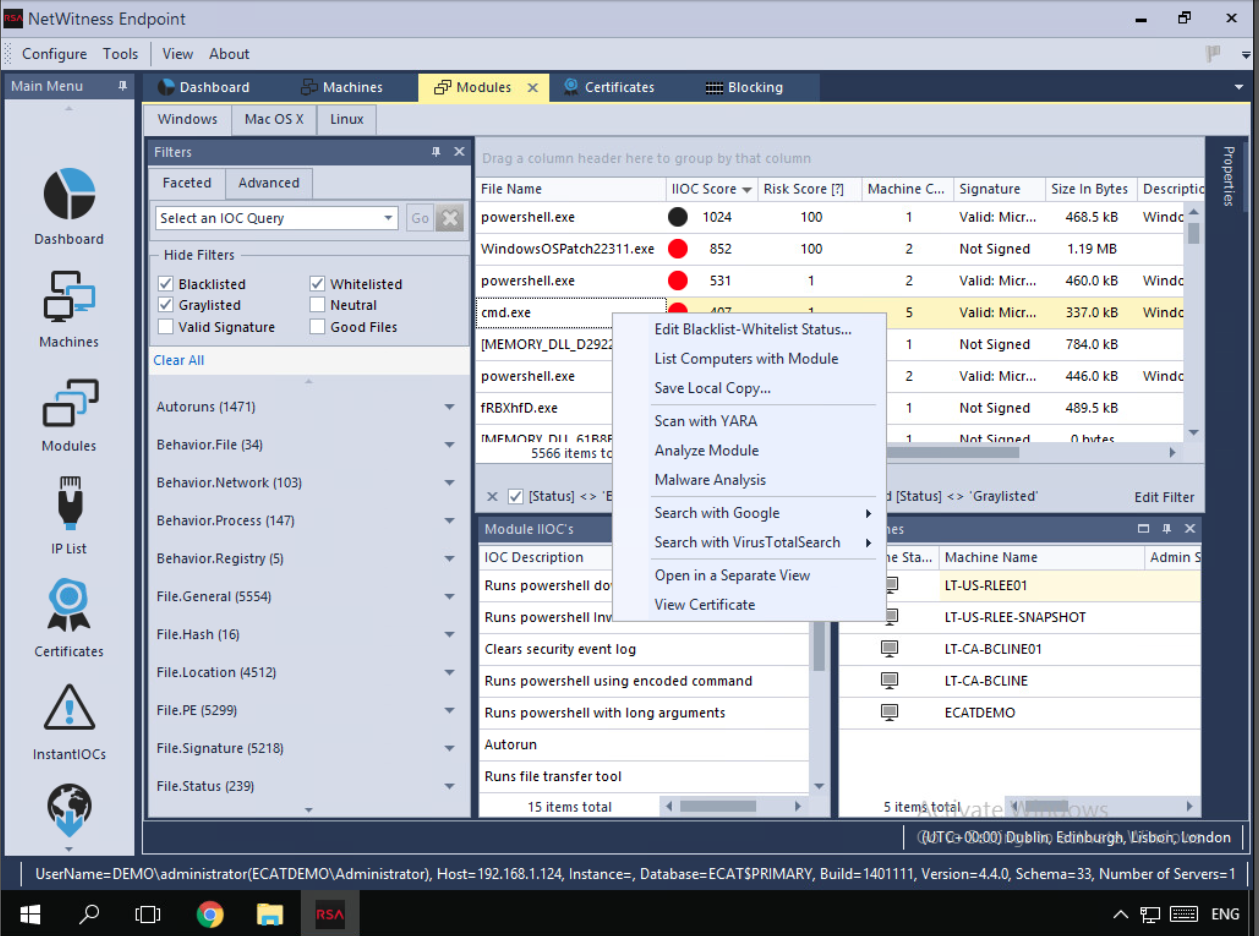
Endpoint before I took over
Planning
Before the release I realised we could include some easy to build features like Google and VirusTotal Lookup if we built Context menu (right click)/More action onto a file. This would also make actions more accessible. After discussions with my Product Manager I decided to push for its need along with a consistent Action bar, Filter Panel etc. for Files view first.
So, one cycle was used to build and test these new patterns, while the next shortened cycle (due to Christmas holidays) was used to scale and re-use them across the interface. This also meant that by starting with Files, most of the implementation issues could be ironed out in Cycle 9 and re-using it in Cycle 10 for Hosts would be easier.
Interaction patterns I added and were re-used across -
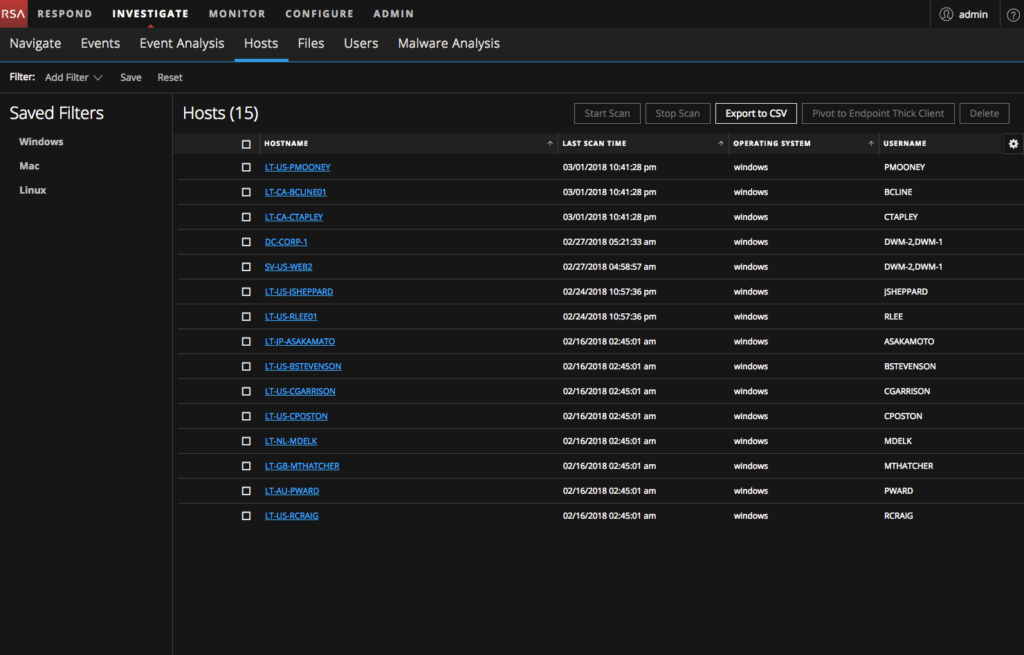
- Consistent action bar above Hosts and Files that included a dropdown for More Actions that will be added in subsequent releases
- Right click context menu for all tables that mirrored the actions from Action bar making accessibility to them easier
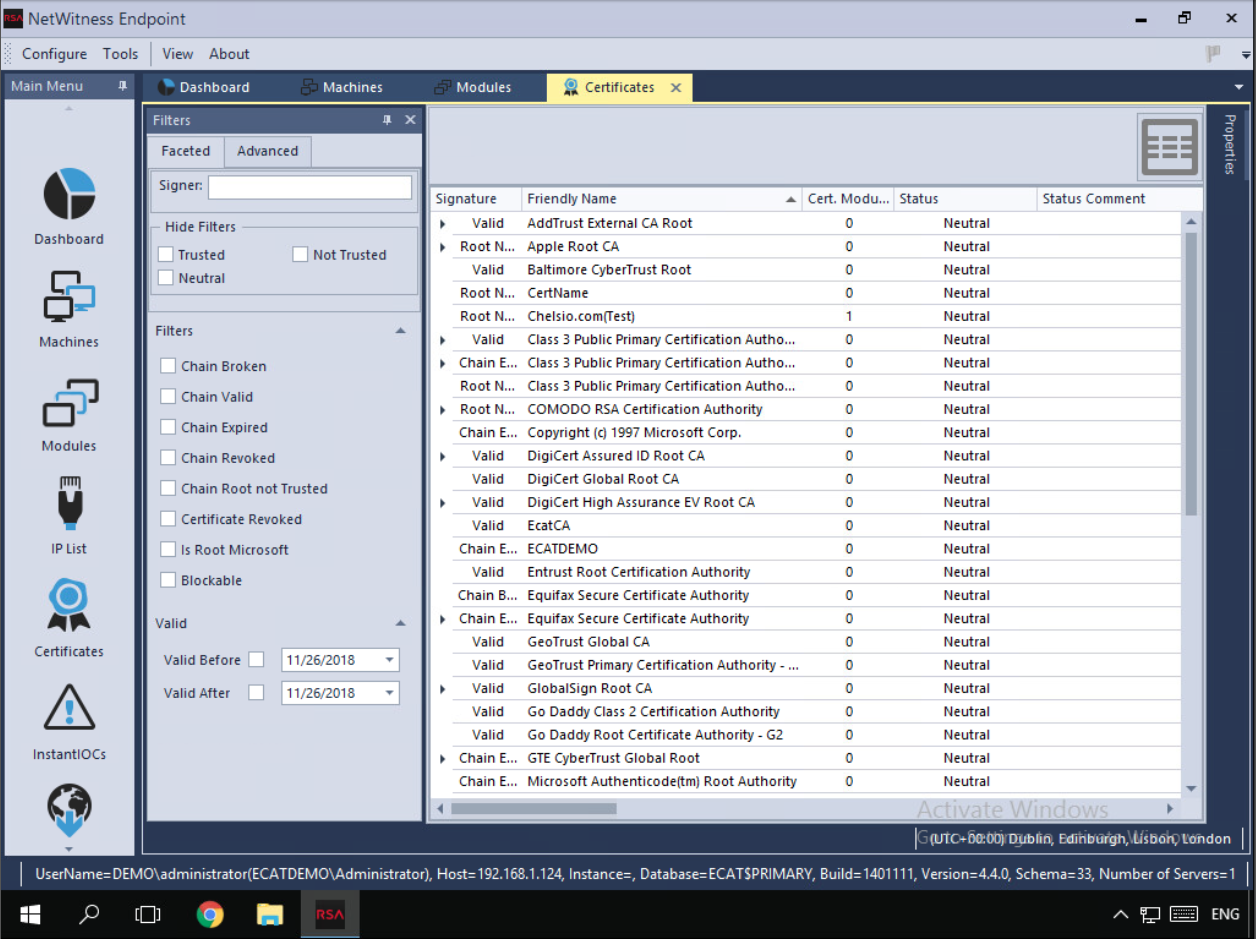
- Sliding panel on right click from a table – initially designed for Certificates view but reused for improving the usability in Process details and other features File Analysis and MFT.
- A downloads column which showed download status and error description on hover – introduced for Files download and later re-used for the Agent Command History feature and for MFT
- Three column layout that included a downloaded drive’s reconstructed view with options to filter on.
- Condition based tool tips on buttons to let users know current state of inactivity and possible steps to activate button
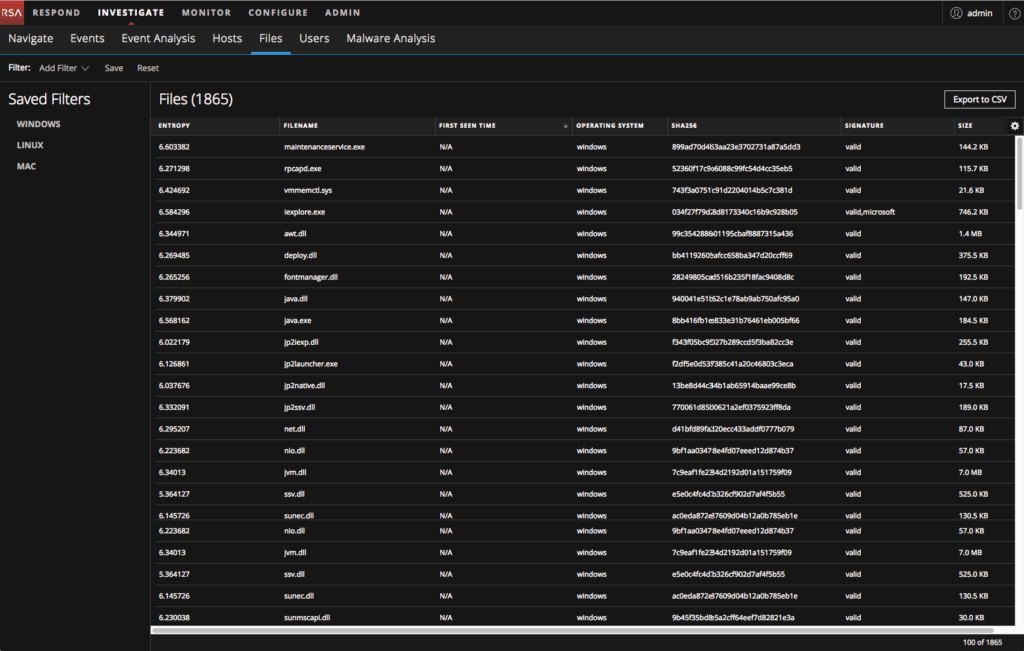
- Re-designed Host and Files details pages with primary actions visible and described as icons and secondary actions in a menu with flyout options
- Multiple minor enhancements to tables like hover effect, selection details etc.
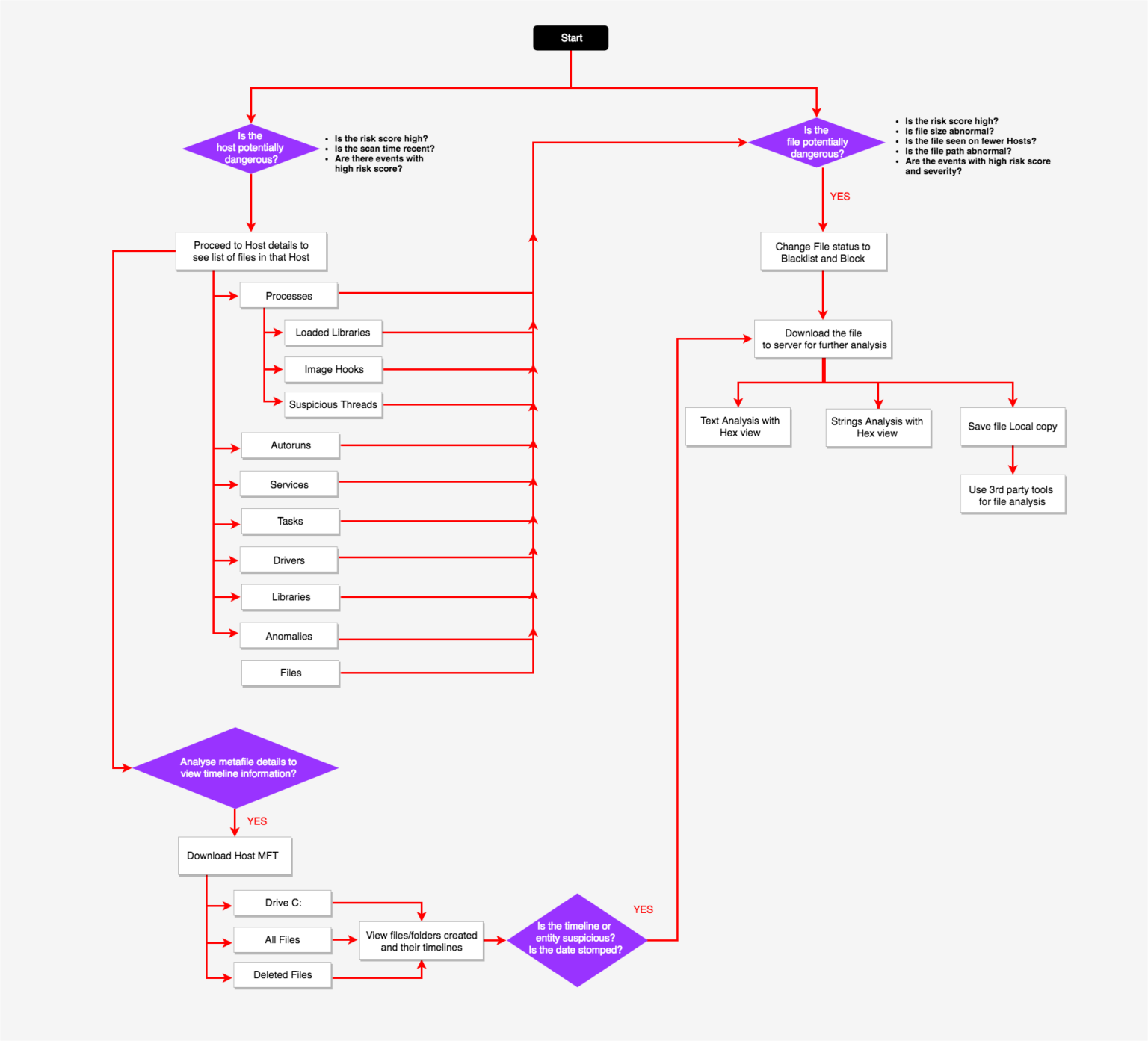
File Status & Blocking
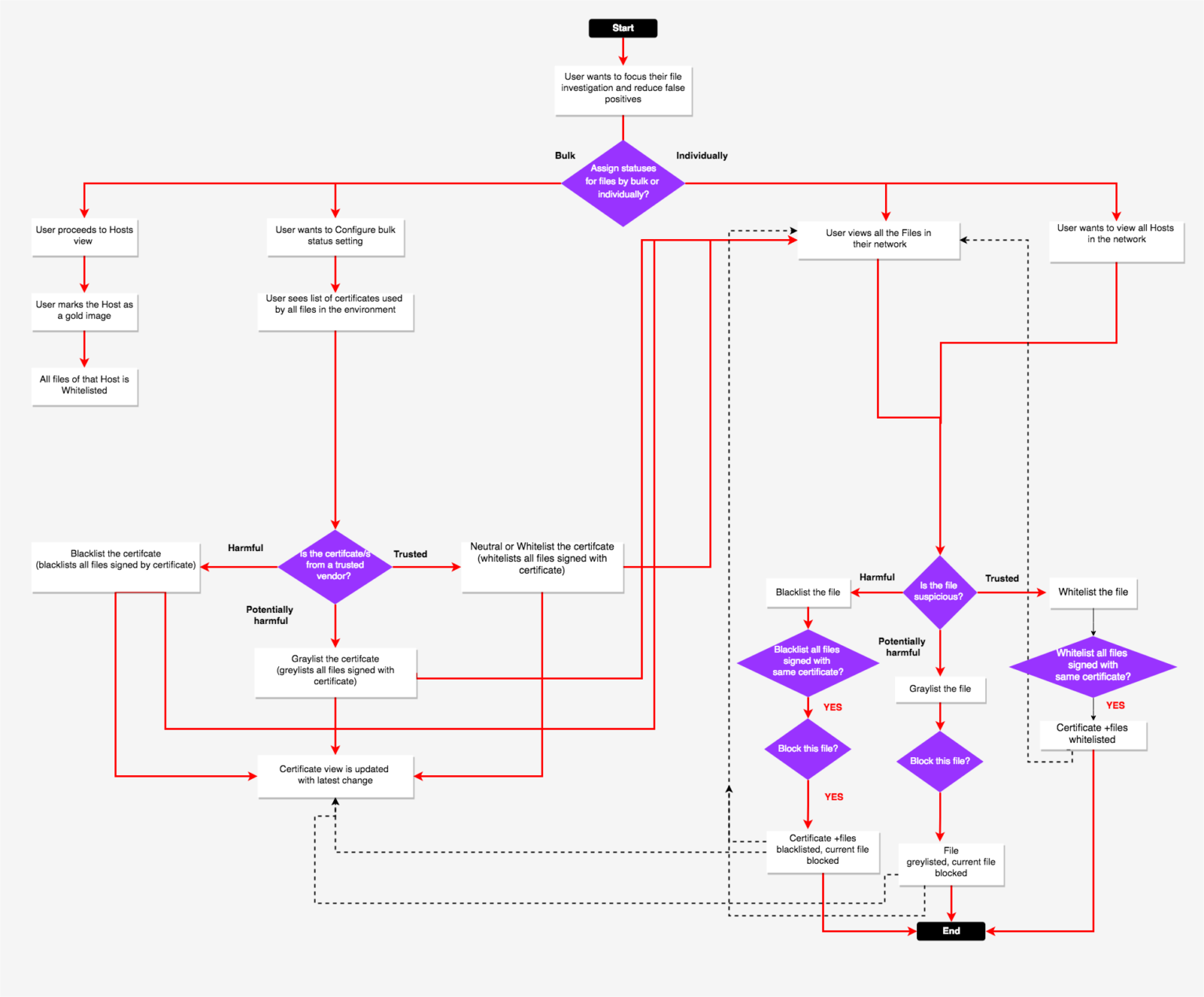
Analyst needs a way to automatically or manually tag Files into different bias status (Blacklist/Graylist/Whitelist/Neutral) to help focus investigations on threats that actually matter by reducing false positives/noise, eliminating known good files. They should also have the means to prevent a file from accessing any OS resources ("blocking" - Blocking prevents a file from executing as a process, as well as running in a scripting environment) and unblock them too.
File Analysis
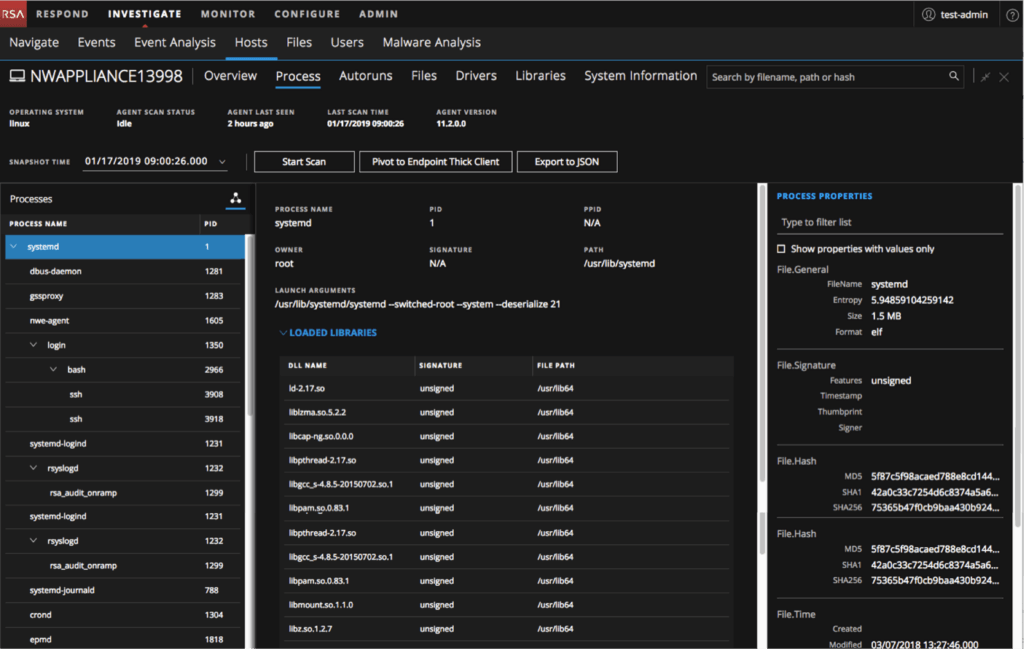
Allow files to be downloaded for deeper analysis. When a suspicious file is found (this could be based on high Risk Score, abnormal score, activity on number of hosts etc.) its is first downloaded to the main server. Once downloaded additional options like viewing and searching for strings in executable, viewing imported libraries and functions, viewing binary content and allowing local copy save for further analysis with 3rd party tools is possible.
Master File Table (MFT) Analysis
To follow up on any suspicious or confirmed malicious file finding, allow MFT analysis of a host. MFT analysis provides a complete view of what may have introduced the file under investigation on the system, as well as what other activity occurred before and after the file appeared on the system. MFT be automatically collected during particular scans, or driven by certain events.
Host Isolation
Host containment feature allows an analyst to isolate a machine that may be compromised. Applying containment blocks the ability of a machine to connect to the network, allowing the analyst to observe the malware in action while protecting the larger environment. Analysts are able to control the spread of an attack and investigate the malware behavior post-containment. When a machine is contained, analyst can provide a list of allowed IP/Hostnames to which the contained machine can communicate with along with the default list of allowed connections like the NW Endpoint, DNS Servers etc.
Kudos to the endpoint team!
Ran through the new NWE and to be honest with you its looks much improved from the current NWE.
I really don’t see anything from my perspective that I would be wanting. I like the flow of it and the ability to pivot from an event to a number of different areas. The process event details are great and the ability to pivot into process analysis and see the actual process flow from there is great.
As far as investigation and managing files, this seems so much more easier than the old system. The search functionality seems much improved and the drill down and pivot ability is vastly improved. Like that I can see other hosts that might contain that file much more easily. Again, I am not seeing any missing information that would hinder an investigation.”
“From my limited experience hunting with the tool, compared to NWE 4.4.x which we are currently on, 11.3 is huge jump forward in terms of process flow, event details and ease of use.
Nothing pops out as missing, although I’m sure as we get more acquainted with the new UI, little things will pop up as possible enhancements.”